Now that the Digital Operational Resilience (DORA) is being reviewed by regulators, the question facing banks, insurance companies, and the third parties they work with has shifted from “Are we compliant?” to “Can we prove it, and can we sustain it?” The regulation demands more than policy updates or one-time exercises; it calls for a deeply embedded, organisation-wide approach to operational resilience, with executive accountability and measurable outcomes.
To help you assess where you stand and what may need recalibrating, the team of advisors at Fusion has developed a six-point checklist focused on the five key pillars of DORA. Whether you’re refining mature processes or addressing emerging gaps, this checklist is designed to support a more confident, coordinated path forward for achieving operational resilience for financial services.
The DORA Readiness Check: Is Your Organisation Prepared?
-
Are You Taking a Cross-Functional Approach?
DORA requires oversight of multiple domains: cybersecurity, disaster recovery, third-party risk, incident response, business continuity, and more. In practice, that means multiple teams must work together to deliver the required compliance activities.
Ask your team to prove:
- Is there an executive sponsor with oversight across departments?
- Do your resilience efforts involve input from technology, operations, compliance, legal, and risk functions?
- Is there a unified governance structure guiding DORA-related initiatives?
Why it matters: Fragmented ownership leads to gaps and under DORA, gaps equal the risk of non-compliance.
-
Is Your ICT Risk Management Framework Fit for Purpose?
DORA requires that financial entities and their ICT third-party providers implement a comprehensive risk management framework. Risk management efforts should centre on critical systems, with clear processes for identifying, evaluating, and reducing potential threats.
Hold your team accountable by asking:
- Are critical services and digital dependencies end-to-end?
- Are operational risk assessments updated regularly and based on real-world conditions?
- Is your approach adaptable as new threats or technologies emerge?
Why it matters: A static or outdated risk framework puts compliance and continuity, at risk. Strong frameworks are now the baseline for operational resilience in financial institutions.
-
Have Impact Tolerances Been Evaluated?
DORA formalizes the use of impact tolerances, which are the maximum level of disruption organizations can endure to their critical business functions before causing intolerable harm to the market, customers, or the firms themselves. While the concept isn’t new, it’s now embedded in regulation. This means that what was once a best practice is now a baseline requirement.
To set meaningful impact tolerances, firms must first identify the services essential to their operations, referred to as critical business services or Critical and Important Functions (CIFs) under DORA. Clearly defining these functions is crucial, as they provide the basis for applying and testing impact tolerances effectively.
Ask your team:
- Have you defined impact tolerances for each critical business service?
- Have you conducted scenario testing or simulations to validate these assumptions?
- Do you have visibility into these reports and findings at the executive or board level?
Why it matters: Regulatory requirements aside, this is core business intelligence. You can’t manage what you haven’t measured.
-
Is Your Incident Reporting Process Ready to Withstand Real Pressure?
DORA sets a high bar for incident reporting and it’s not just about having a process in place. The regulation includes detailed Regulatory Technical Standards (RTS, which are legally binding technical rules developed by European Supervisory Authorities to specify how legislation should be applied in practice, and Implementing Technical Standards (ITS) that define what must be reported, when, how, and in what format.
At the core of the reporting process is a structured timeline:
- Firms have up to 24 hours from the moment an ICT-related incident is detected to assess and classify
- If classified as major, an initial notification must be submitted to the national competent authority (NCA) designated in each EU member state (which includes the European Banking Authority (EBA), European Securities and Markets Authority (ESMA), and European Insurance and Occupational Pensions Authority (EIOPA) within 4 hours
- A more detailed intermediate report is then required within 72 hours of detection
While based on the principles of the NIS2 Directive, which is an EU-wide framework aimed at strengthening cybersecurity across critical sectors, these timelines are adapted under DORA to meet the specific needs and operational scale of financial institutions. For significant cyber events, similar reporting obligations apply, requiring both urgency and accuracy.
The ITS provides standardised forms, templates, and reporting procedures, while detailed guidance in the framework outlines the specific data points that must be included in each stage of reporting.
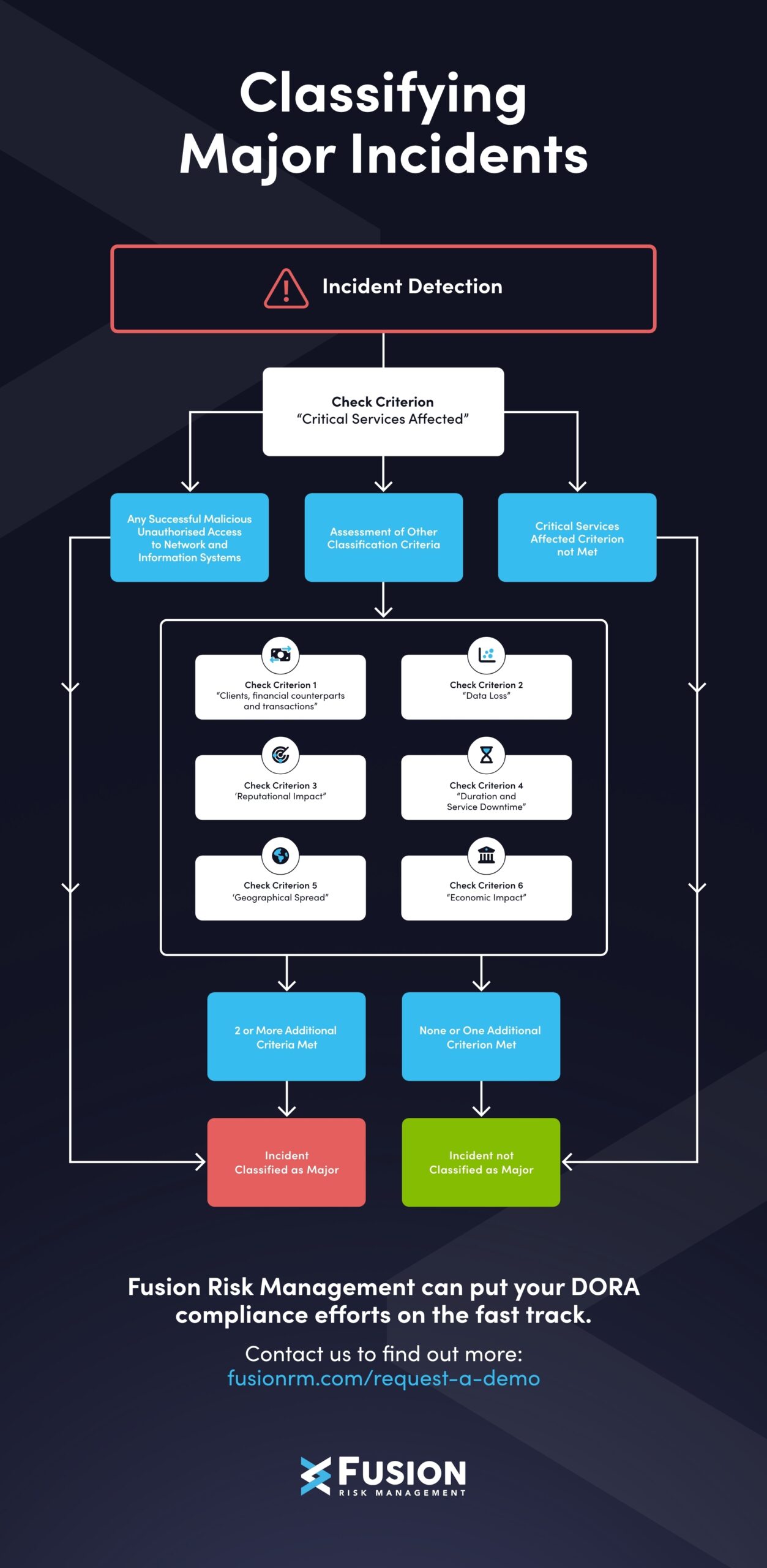
Ask your team:
- Are there implemented reporting workflows that align with DORA’s RTS and ITS, including time-bound alerts and structured data collection?
- Is your team trained to identify major ICT-related incidents and classify them appropriately within 24 hours of detection?
- Are you ready to submit structured reports to competent authorities within the required timeframes, starting at just 4 hours post-classification?
- Have your procedures been tested under real or simulated conditions to confirm reliability and clarity across departments?
Why it matters: Under DORA, incident reporting is more than just a compliance item; it’s also a demonstration of your organisation’s operational maturity. Regulators expect more than reactive notifications. They want timely, complete, and standardised reports that reflect coordinated internal processes. Getting this right requires more than tools. It requires training, alignment, and practice.
-
Are You Managing Third-Party Risk with Full Transparency — Including the Register of Information?
DORA places substantial regulatory weight on how financial entities manage their ICT third-party risk. It’s not enough to perform initial due diligence or draft strong contracts — organisations must maintain continuous oversight and provide evidence of it.
A key part of this oversight is the mandatory Register of Information (RoI). Under DORA, all financial entities must maintain an up-to-date, detailed inventory of their contractual arrangements with third-party ICT service providers — particularly those supporting critical or important functions.
The RoI must include:
- The name and role of each provider
- The services delivered and their criticality
- The location of data processing and service delivery
- Sub-outsourcing arrangements
- Dates, renewal terms, and termination clauses
Review with your team:
- Have you identified and mapped all third-party ICT providers, especially those supporting critical functions?
- Are DORA-specific obligations—like rights to audit, data access, and termination for non-compliance—clearly reflected in contracts?
- Is your RoI complete, regularly maintained, and aligned with the reporting expectations of your competent authority?
- Are you actively monitoring third-party performance and resilience — not just during onboarding, but continuously?
Why it matters: Third-party ICT failures can create operational, reputational, and regulatory fallout in seconds. DORA recognises this and requires proactive, structured oversight. The RoI is not just a regulatory formality—it’s a living record of your digital supply chain. Keeping it accurate, comprehensive, and aligned with your risk posture is fundamental to demonstrating compliance and ensuring resiliency.
-
Are You Resourced for Ongoing “Run State” Management?
Compliance doesn’t end with implementation. DORA is a long-term operational commitment. As systems evolve, staff rotate, and threats appear, the ability to maintain operational resilience in financial services will depend on continuous attention and resourcing.
Ask your team:
- Have you planned for the operational workload that follows initial compliance?
- Are there dedicated roles or teams checking ongoing adherence?
- Is digital resilience integrated into wider strategic and transformation initiatives?
Why it matters: Sustained compliance is about culture and consistency — not just checklists.
Understanding Resilience as a Strategic Asset
It’s worth repeating: DORA isn’t just a regulatory burden. When approached thoughtfully, it becomes a blueprint for long-term organisational strength. Financial institutions already invest heavily in risk management, cybersecurity, and business continuity.
Technology plays a critical role here. From real-time monitoring and automated reporting to system mapping and incident response, the right tools help ensure that compliance isn’t just a one-time effort, but a living, evolving process. DORA rewards organizations that take a clear, collaborative, and consistent approach, which is something technology makes possible at scale.
Whether you’re building from the ground up or fine-tuning mature processes, regular check-ins like this are essential. They help improve operational resilience for financial services and ensure that supporting technologies continue to evolve alongside your organization and stay aligned with a fast-changing regulatory and threat landscape.
If you’re looking to evaluate your current DORA posture — or if you’re unsure where the gaps are — we’re here to help. Reach out to us today to explore how Fusion’s solutions can help your organization navigate risks and meet evolving regulatory requirements.
Quick Self-Assessment: 5 Yes/No Questions
- Can we show clear board oversight of our DORA programme?
- Have we documented our critical ICT dependencies, both internally and externally?
- Are we confident in our incident detection and reporting procedures?
- Do we have defined impact tolerances, and have we tested against them?
- Is our compliance programme future-ready — built to sustain, not just survive?




